Cybersecurity
Basic approach
Damage caused by increasingly sophisticated cyberattacks is on the rise. Breaches of personal information held by corporates and a record amount of unauthorized money transfers from phishing are some examples witnessed in 2023. At Mizuho, we are continuously pressing forward with cybersecurity measures as per our Declaration of Cybersecurity Management, to allow customers to use our services with the peace of mind that they are secure.
Declaration of Cybersecurity Management
Governance system
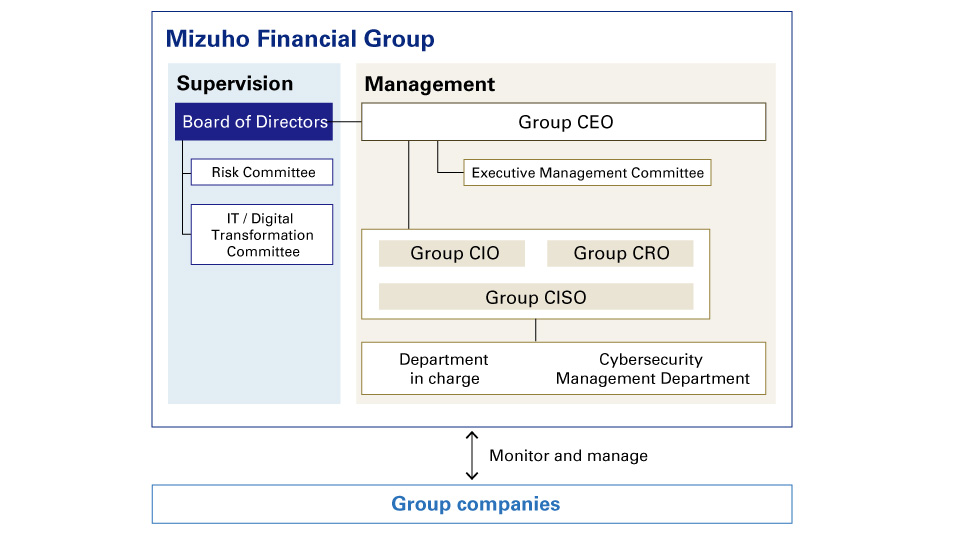
At Mizuho, we have established the position of Group Chief Information Security Officer (Group CISO), who administers overall group-wide / global cybersecurity management. In the interest of clarifying how the check-and-balance system applies to the Group Chief Information Officer (Group CIO) as part of our second line of defense, the Group CISO reports to both the Group CIO and Group Chief Risk Officer (Group CRO). We are striving to enhance our cybersecurity posture by implementing this system of double reporting. The Group CISO, as the person responsible for cybersecurity risk management, reports to the Executive Management Committee and Board of Directors the progress of the various measures taken, and works with management to review cybersecurity policies and resource allocation in a timely and appropriate manner.
We have appointed a person in charge of cybersecurity and have established a communication system at group companies, to monitor the status of our cybersecurity measures and to quickly gather information when an incident occurs.
Incident response
Our specialist units, particularly SOC1 and Mizuho-CIRT2, work closely with external specialized organizations to respond to cybersecurity incidents. SOC detects suspicious activity to identify potential threats using a 24-hour, 365-day monitoring framework, while Mizuho-CIRT shares information with internal and external partners to better handle incident response, investigation, and recovery based on the information received from SOC.
These specialist units have established a procedure for responding to different cyberattack methods, and are constantly conducting internal and external training and drills to properly respond to any incident.
- Security Operation Center (a specialized team that monitors and analyzes threats to information systems in organizations such as other corporates)
- Cyber Incident Response Team (incident response teams that specialize in information security issues within the organization)

Surveillance at a location outside Japan
Cybersecurity measures
Our cybersecurity measures include group-wide, global, and supply chain scopes. In order to identify and prevent cybersecurity risks, we collect threat intelligence from public institutions, trusted communities, the media, and other sources, and prioritize measures based on potential impact on our company.
Modern systems are constantly exposed to a wide variety of security threats. We take measures to ensure consistent security throughout the system development lifecycle, from planning through development and operation.
Our systems have a virus analysis and a multi-layered defense mechanism, and we are working to strengthen our resilience by implementing TLPT1 to test the effectiveness of these technical measures and the effectiveness of the response process.
In order to evaluate the maturity of these cybersecurity measures, we refer to third party assessment by the Cybersecurity Assessment Tool of the Federal Financial Institutions Examination Council and the Cybersecurity Framework of the National Institute of Standards and Technology.
- Threat-Led Penetration Testing (evaluation of systems and response processes by analyzing targeted threats and simulating attacks)
Cybersecurity personnel development
We periodically test the group's ability to respond appropriately to a cyber incident, and thoroughly eliminate any issues identified. We consider this process vital in order to strengthen individual and organizational incident response capabilities.
To ensure that every executive officer and employee has the necessary cybersecurity awareness, knowledge, and skills, we employ internal and external training, exercises, and drills including incident response training for management and other staff, role-specific cybersecurity training, and biannual phishing email training for all executive officers and employees.
We actively support employees in acquiring professional qualifications and encourage professional development through external specialist programs. In addition, we actively recruit professionals, and have established an IT system course for new graduates hired in Japan, in order to acquire and develop personnel with advanced expertise.